Can a redactor transform the data? Replace memos by their hashes for example?
For the last week, we are mainly working on PCZT together with the Zashi team.
The Zashi team has proposed an an implementation of PCZT. We are having close discussions with them: pczt: Define the structure and semantics of the PCZT format by str4d · Pull Request #1577 · zcash/librustzcash · GitHub
For the last week, we mainly focused on reviewing the definition of PCZT and conducting corresponding code experiments.
We will continue the development work next week.
This week, we developed on Keystone based on the PCZT data structure proposed by the Zashi team:
- Completed the transaction hash calculation logic
- Completed the definition and implementation of PCZTSigner on the Keystone side
Meanwhile, Zashi team is working on the rest fileds definitions on PCZT(like derivation paths) also the encoding of PCZT.
Next week, we will conduct an end-to-end verification for current PCZT implementation and develop the UI for the signing process.
Current development status: [WIP]Feat/zcash by soralit · Pull Request #1366 · KeystoneHQ/keystone3-firmware · GitHub
This week, we completed the E2E verification of PCZT: we obtained the parameters of PCZT in the command line wallet, restored these parameters in Keystone, calculated and compared the hash for co-signing, and after the signature was returned to the command line wallet, the transaction was successfully broadcasted to the blockchain (txid: ac4d40827d1963b6f6e5fb56d61e96bf799bafbc889fdcc865f4d1de3779f187).
We are currently developing the UI logic for transaction parsing and signing on Keystone.
Great work. What’s the ETA until release?
We just had a call with Zashi team last night as we have done most of the dev work on our end and now it’s getting into “real” integration.
We are aiming at releasing the integration before Christmas. And this is TOP priority on both ends.
Any one can help?
Where can I post the designs?
Hey bro please follow the instructions here Notion – The all-in-one workspace for your notes, tasks, wikis, and databases.
Last week,
- we had a meeting with the Zashi team to discuss how to develop iOS and Android software wallets for the upcoming integration, and we agreed on the delivery timeline for the Keystone SDK. More details - x.com
- The development of the Keystone Firmware continued. We improved the verification logic and some parsing logic for Zcash transactions to ensure that transaction information is safe and transparent for users.
It is the BC-UR standard, which is widely adopted for use with Bitcoin. See here for some sample code I used to test QR sizes and number of frames for various file sizes (this is not tested for interoperability).
Last week, we communicated with the Zashi development team and fixed some existing development issues. Meanwhile, the Keystone team has entered the final UI development phase for Zcash and resolved some runtime issues introduced after integrating Zcash.
If I purchase a Keystone hardware wallet now, can it only support Zcash t-addresses? Recently, Keystone is offering a 20% discount, so I’m considering buying one. Could you provide more information?
they plan to support all shielded pools.
just atm they dont yet support any Zcash, they are building that all - soon to be ready.
Pre-orders will be accepted soon
Zcash full support is WIP now. Hopefully we can deliver that together with Zashi team soon (can’t make a solid promise here).
And you can purchase with the 20% off BF discount on our website now.
Or we are launching a Zcash co-branded version tomorrow, it will be $149.
You can check the design here - x.com
Last week we have done -
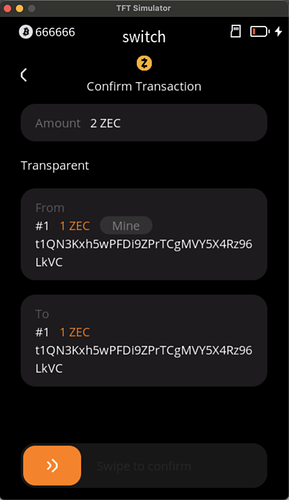
- This week we completed the UI development (based on mocked data) for Zcash PCZT on Keystone firmware.
- We provided iOS and Android SDKs to the Zashi team for subsequent software development.
- The Zashi team is finalizing the PCZT encoding format definition, after which we will make the final modifications to the firmware.
You can check some of the UI on Keystone here -
Last week, the Zashi team completed the PCZT implementation and synchronized it with us. We have updated the relevant dependency code and adjusted the corresponding business logic.
Currently, we are able to parse a PCZT that has been encoded using the postcard encoding format.
Next week, we will continue to complete the remaining code work and distribute a beta package to the Zashi team for subsequent integration development work.